# CVE-2025-8088: WinRAR NTFS ADS Path Traversal Vulnerability Analysis
CVE-2025-8088: WinRAR NTFS ADS Path Traversal Vulnerability Analysis
I was catching up on the weekend’s news when I saw a fantastic report from ESET pop up covering (yet another) rar file path traversal vulnerability. At first it seemed like there wasn’t going to be any details to dig into given the reports are careful not to describe the vulnerability in too much detail as to deter copy cat attackers. Also, interestingly, there is a fake poc on github which does not represent this CVE at all but I assume the author couldn’t resist the call of sweet sweet SEO (much like this author). However, I did find one of the file hashes in a sample submitted to any.run.
Fantastic! Let’s go!
First, it seemed like nothing had happened as there were no obvious malicious network traffic generated, but on deeper inspection of any.run’s report, I noticed a lnk file was launched in the “behavior activities” view.
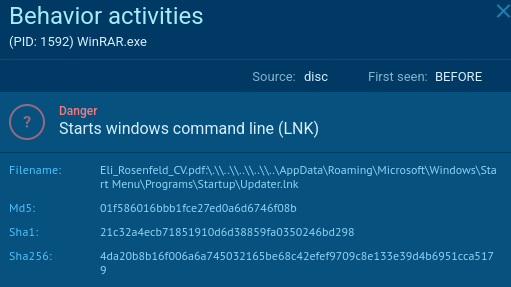
This led me to look closer at the rar file iteslf and sure enough…
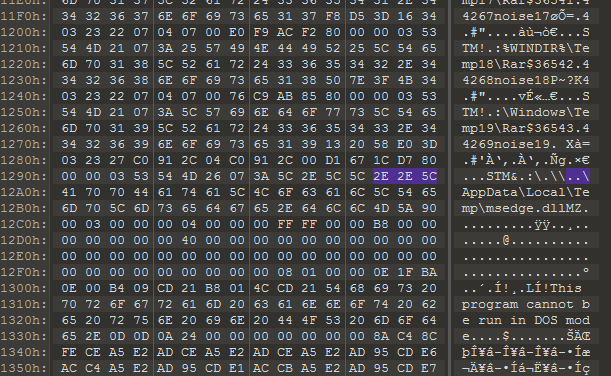
Here we can see the malicious bytes in action. According to rarlab.com STM section is NTFS alternate data stream so sure enough that matches the reported details from ESET.
From there, it was simple to create yara & suricata detection to find the /\x00\x00\x03STM.{2}\x3a[^\x00]*\x2e\x2e\x5c in network and file bytes.
suricata rules:
Thanks to James Emery-Callcott of Emerging Threats for adding a more durable path traversal PCRE: /\x2e\x2e\x5c/ => /^.{0,10}(?:\x2f|\x5c|%5[Cc]|%2[Ff])?(?:(?:\x2e|%2[Ee]){1,2}(?:\x2f|\x5c|%5[Cc]|%2[Ff]){1,}){2,}/
# note {,64} prevents runaway pcre, tune as desired
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"CORELIGHT EXPLOIT RAR File ADS Path Traversal Inbound via HTTP (CVE-2025-8088)"; flow:established,to_client; http.response_body; content:"STM"; fast_pattern; pcre:"/^.{2}\x3a[^\x00]{0,64}(?:\x2f|\x5c|%5[Cc]|%2[Ff])?(?:(?:\x2e|%2[Ee]){1,2}(?:\x2f|\x5c|%5[Cc]|%2[Ff]){1,}){2,}/R"; reference:url,travisgreen.net/2025/08/11/CVE-2025-8088.html; classtype:bad-unknown; sid:7704721; rev:1;)
alert http2 $EXTERNAL_NET any -> $HOME_NET any (msg:"CORELIGHT EXPLOIT RAR File ADS Path Traversal Inbound via HTTP2 (CVE-2025-8088)"; flow:established,to_client; http.response_body; content:"STM"; fast_pattern; pcre:"/^.{2}\x3a[^\x00]{0,64}(?:\x2f|\x5c|%5[Cc]|%2[Ff])?(?:(?:\x2e|%2[Ee]){1,2}(?:\x2f|\x5c|%5[Cc]|%2[Ff]){1,}){2,}/R"; reference:url,travisgreen.net/2025/08/11/CVE-2025-8088.html; classtype:bad-unknown; sid:7704722; rev:1;)
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"CORELIGHT EXPLOIT RAR File ADS Path Traversal Inbound via raw tcp (CVE-2025-8088)"; app-layer-protocol:!http; app-layer-protocol:!http2; content:"|00 00 03|STM"; fast_pattern; pcre:"/^.{2}\x3a[^\x00]{0,64}(?:\x2f|\x5c|%5[Cc]|%2[Ff])?(?:(?:\x2e|%2[Ee]){1,2}(?:\x2f|\x5c|%5[Cc]|%2[Ff]){1,}){2,}/R"; threshold:type limit, seconds 600, count 1, track by_src; reference:url,travisgreen.net/2025/08/11/CVE-2025-8088.html; classtype:bad-unknown; sid:7704723; rev:1;)
yara rule:
rule CVE_2025_8088_rar_ADS_traversal {
meta:
description = "Detects CVE-2025-8088 WinRAR NTFS ADS path traversal exploitation"
author = "Travis Green <travis.green@corelight.com>"
reference = "https://www.welivesecurity.com/en/eset-research/update-winrar-tools-now-romcom-and-others-exploiting-zero-day-vulnerability/"
date = "2025-08-11"
version = "1.0"
hash1 = "107f3d1fe28b67397d21a6acca5b6b35def1aeb62a67bc10109bd73d567f9806"
tlp = "WHITE"
strings:
$x1 = "STM" fullword ascii
$x2 = "..\\\\" fullword ascii
$x3 = /STM..\x3a[^\x00]*\x2e\x2e\x5c/ ascii
condition:
uint16(0) == 0x6152 and 3 of ($x*)
}
There’s certainly much much more to be said about the file that is launched and TTPs around the campaign, but this will have to do for today. Also, shout out to Winrar developers, you have an amazing track record considering it’s been around more than 30 years..